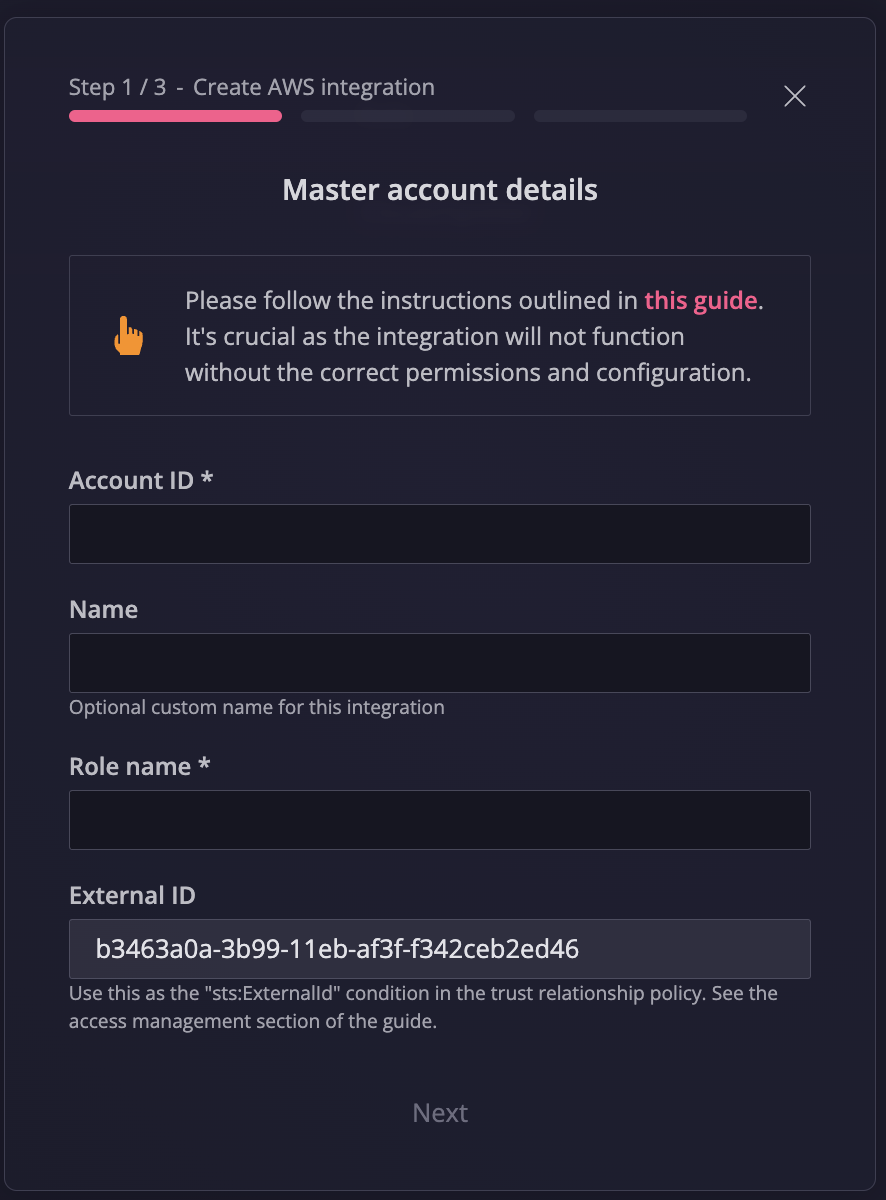
AWS Access Management
Example codes are in Terraform HCL. Decide a name for an AWS role to use. Spotter will ask the name when creating an integration setup.
Configure Master Account
Create a role named YOUR_ROLE_NAME into your master account with the following permissions
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "",
"Effect": "Allow",
"Action": [
"ce:GetCostForecast",
"ce:GetCostAndUsage",
"ce:GetReservationPurchaseRecommendation",
"ce:GetRightsizingRecommendation",
"ce:GetSavingsPlansPurchaseRecommendation",
"ce:GetTags",
"ce:ListCostAllocationTags",
"config:ListAggregateDiscoveredResources",
"iam:ListAccountAliases",
"organizations:ListAccounts",
"support:DescribeTrustedAdvisorChecks",
"support:DescribeTrustedAdvisorCheckSummaries"
],
"Resource": "*"
}
]
}Configure Config Account
Create a role named YOUR_ROLE_NAME into your config account with the following permissions
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "",
"Effect": "Allow",
"Action": [
"config:ListAggregateDiscoveredResources",
"iam:ListAccountAliases",
"support:DescribeTrustedAdvisorChecks",
"support:DescribeTrustedAdvisorCheckSummaries"
],
"Resource": "*"
}
]
}Configure Security Account
Create a role named YOUR_ROLE_NAME into your security account with the following permissions
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "",
"Effect": "Allow",
"Action": [
"iam:ListAccountAliases",
"securityhub:GetFindings",
"support:DescribeTrustedAdvisorChecks",
"support:DescribeTrustedAdvisorCheckSummaries"
],
"Resource": "*"
}
]
}Configure Other Accounts
Create a role named YOUR_ROLE_NAME into all other accounts with the following permissions
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "",
"Effect": "Allow",
"Action": [
"iam:ListAccountAliases",
"support:DescribeTrustedAdvisorChecks",
"support:DescribeTrustedAdvisorCheckSummaries"
],
"Resource": "*"
}
]
}Configure Trust Relationship
Create trust relationship for the role from AWS account of Spotter
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "",
"Effect": "Allow",
"Principal": {
"AWS": [
"arn:aws:iam::730660357973:root"
]
},
"Action": "sts:AssumeRole",
"Condition": {
"StringEquals": {
"sts:ExternalId": "YOUR_EXTERNAL_ID"
}
}
}
]
}You’ll find the YOUR_EXTERNAL_ID value from Spotter: Go to Admin → Integrations → AWS → Add New